This week concludes the three-part Blockchain series written by our very own entrepreneur-in-training, Adriel.
In the previous two weeks, Adriel spoke about smart contracts and tokens. This week, we dive into the origins of the “crypto” in cryptocurrencies (digital money based on Blockchain).

Cryptocurrency (or crypto for short) is a word spliced together by two completely different concepts, namely cryptography and currency.
Many people who buy or transact in crypto don’t usually think about the underlying cryptographic processes that take place in order to make the transaction happen.
So, what exactly is cryptography? How does cryptographic processes power what we now know as cryptocurrencies?
It’s time to demystify cryptography in cryptocurrencies!
What is cryptography?
Cryptography is the practice and study of secure communications in the presence of third parties. The whole point of cryptography is to prevent unwanted parties from accessing information that they are not supposed to access.
Since the birth of handwritten texts, people have been finding ways and means to encrypt their information away from prying eyes and ears. The ancient Egyptians carved hieroglyphics on the walls, while the ancient Greeks, Romans and Indians made use of ciphers to secure their messages.
All these changed upon the advent of the computer. The first use of a computer (by Alan Turing) for the purposes of breaking or “brute forcing” was the Enigma Machine used in World War II to decrypt German messages sent over radio waves.

A brute force attack literally means trying all possible combinations in order to break the code or message. It’s humanly impossible to do that with a pen and paper, but with computers, it becomes exponentially easier to break a cipher.
What Kind Of Cryptography Does Cryptocurrencies Use?
There are two kinds of cryptography — symmetric and asymmetric key cryptography.
Symmetric cryptography uses the same key to encrypt and decrypt the message.
On the other hand, asymmetric cryptography requires two keys: a private key and a public key. The private key is kept confidential while the public key can be shown to any person(s).
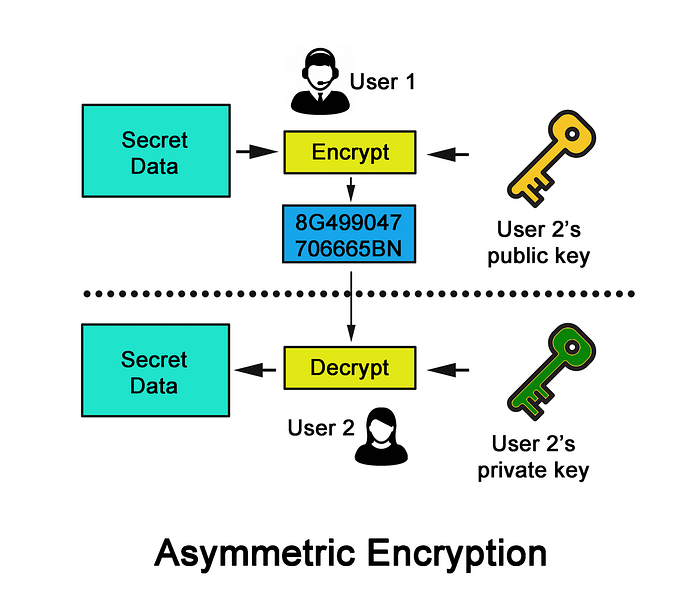
In the illustration above, User 1 (let’s call him Adam) wants to deliver a message over to User 2 (let’s call her Belle) securely, away from prying eyes. Adam first asks Belle to pass him an unlocked padlock while she holds on to her own key that accesses the padlock.
Adam then places the letter into the box with the unlocked padlock and then closes the lock by pushing it. The closed box prevents anyone from reading the letter while being transported.
Once the box gets to Belle, she recognises the box as the one Bob was supposed to pass to her. She then unlocks it with her key and retrieves the message.
Obviously, there is an assumption that no nefarious party intercepts the box and cracks it using “brute force attacks” to retrieve the message meant for Belle.
What is Hashing and How Secure Are Cryptographic Algorithms?
Cryptocurrencies like Bitcoin and Ethereum both use asymmetrical cryptography as part of their technology, so a pertinent question would then be, can someone brute force their way into the information?
While the answer is yes, at current technological levels, it may take a few decades to “brute force” the number, and because it takes so long to brute force into the private key, it is deemed to be very secure.
Since the private key plays such an important role, it has to be:
- Randomly generated
- A long and large number
- Provided by a secure algorithm to generate the keys
Randomisation is extremely important because you wouldn’t want anyone to randomly stumble upon your private key. Long numbers are much harder to brute force compared to shorter ones, and the algorithms need to be proven to be stress-tested against any attacks. One must note that these 3 criteria are constantly being threatened by advancements in computer technology. Quantum computing is that bear in the woods constantly chasing the integrity of encryption algorithms.
For a fully fleshed out analysis of the cryptography of cryptocurrencies, do check out Adriel’s full post here, where he also talks about the cryptographic elements of wallets, digital signatures and tokens.
Until next week, this is VB18 concluding our Blockchain series. Stay safe!
